Zero Trust
Latest about Zero Trust

Anatomy of identity-based attacks
By ITPro published
Whitepaper Helping security teams mitigate identity-based attacks

Supercharge trust for operations
By ITPro published
Whitepaper Innovating through uncertainty
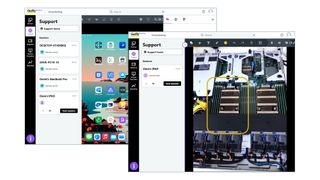
GoTo Resolve Basic review: An SMB-friendly remote support service
By Dave Mitchell published
Reviews This good-value hosted remote support service is ideal for SMBs that demand zero-trust access security

Cloudflare unveils first zero trust SIM for mobile devices
By Daniel Todd published
News New wireless carrier program will also let carriers integrate Zero Trust security into existing corporate plans

Delivering remote zero-trust network access
By IT Pro published
Sponsored Why remote desktop gateways are the modern alternative to VPNs

What is zero trust?
By Gabriella Buckner last updated
In-depth How a zero trust security strategy better protects your business from internal and external attackers

Deloitte launches Zero Trust Access for enterprises
By Praharsha Anand published
News The managed security service protects applications regardless of their location or type

QR codes are just as insecure as anything else
By Davey Winder published
Opinion A browser locked down tighter than a duck’s derriere won’t save you from phishing attacks – but getting to grips with the latest advice and best practice might
Get the ITPro. daily newsletter
Receive our latest news, industry updates, featured resources and more. Sign up today to receive our FREE report on AI cyber crime & security - newly updated for 2024.





